
News
DAAD German Academic Exchange Service
B2 Content Based Authentication
Project Leaders
Prof. Dr.-Ing. Christoph Ruland, Jun.-Prof. Dr.-Ing. Marcin Grzegorzek
Initial Situation
For some years now the use of cryptographic procedures on defective channels is one of the areas of research of the work group Ruland. In this context the work group Ruland has organized a Workshop for ICC 2013 with the title "Information Security over noisy and lossy Communication Systems". So far, two methods have been pursued in the area of image authentication: fault tolerant message authentication codes and content based authentication. Based upon Boncelet, weighted NTMACs (noise tolerant MACs) were introduced, whereby iterative methods were applied to part-blocks, which could not be authenticated, for correction purposes. In 2012 the first publications appeared with the topic of content-based authentication by Han and Chu: For hard or soft authentication, when using error recognition, the same number of DCT-coefficients (decreasing in meaning) are included in the calculation of the cryptographic checksum, as are necessary for the completion of the security and accuracy requirements. In this partial project, instead of the DCT-coefficients other image characteristics are defined, extracted and examined.
Aims and Work Program
The standard method of hard, cryptographic authentication is not very well suited for imaging data, since they remain authentic in spite of changed image values as e.g. in the case of compression. In this partial project approaches to content based image authentication are being developed, which accept permitted image changes. The aim is to reliably execute the authentication of image data on different levels of semantic abstraction. Starting point is the identification of appropriate criteria of perception, which remain intact, with permitted changes of image data. On this basis methods for extraction of feature vectors are to be developed, which represent the criteria of perception numerically. The picture authentication is then to be achieved by means of content based "soft" authentication on the level of feature presentation. Additionally a safety analysis is to be realized, which consider on the several different perception criteria the corresponding levels of trust.
 |
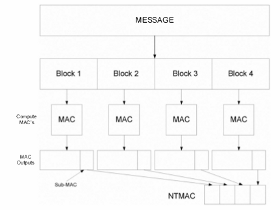 |
| Image Error Correcting Row and Column-wise Message Authentication Code | Noise Tolerant Message Authentication Codes with one partition and four blocks |

